This is part 1 of a four-part series on autonomous vehicle cybersecurity. This part explains the autonomous vehicle software stack, part 2 and part 3 review the various attack vectors and security gaps. Finally, part 4 explains why you need expertise for the development and ongoing risk mitigation of autonomous vehicle firmware.
Modern advances have paved the way for increased autonomous technology in vehicles. This ranges from what are now considered basic features, like anti-lock brakes and stability control, to self-driving capabilities that will replace the steering wheel—and along with it, all human intervention. Across the autonomous vehicle software stack, there are numerous interacting components whose vulnerabilities must be considered as we forge ahead to complete autonomy.
The Six Levels of Autonomy
Before we can dive into the autonomous vehicle software stack, it’s essential to understand how the latest solutions in vehicle technology have given rise to differing levels of autonomy. The Society of Automotive Engineers (SAE) has defined six levels of vehicle autonomy ranging from L0 (no automation) to L5 (full automation).
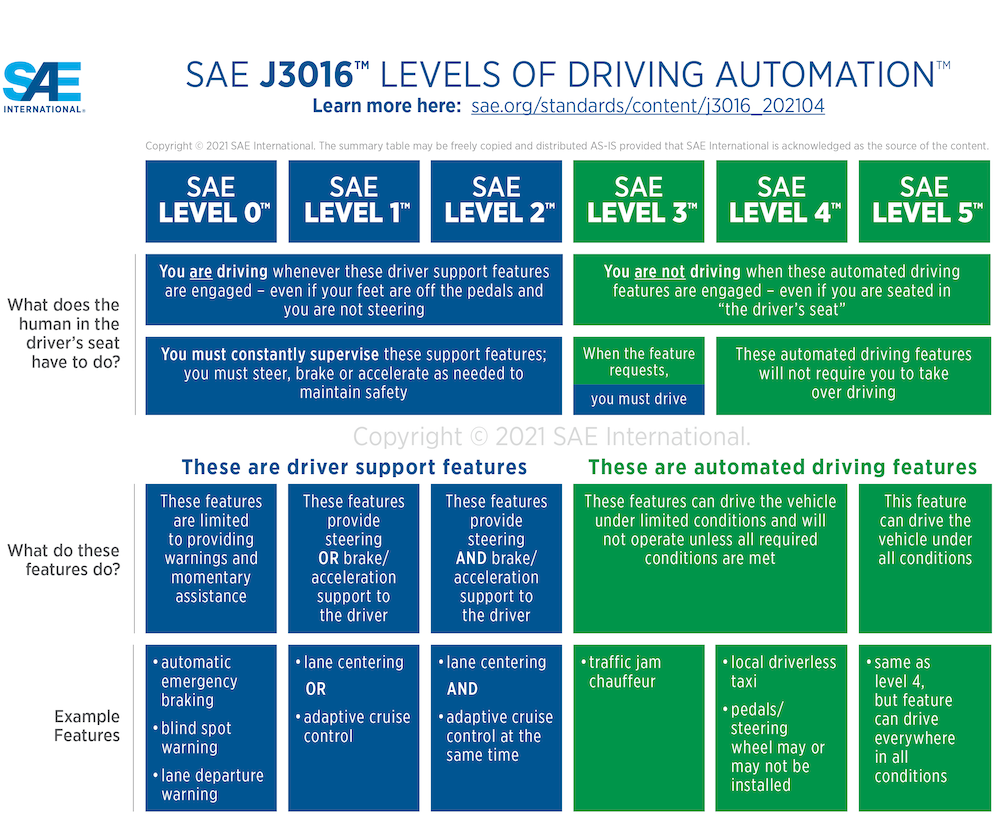
Source: SAE International, SAE Levels of Driving AutomationTM Refined For Clarity and International Audience, May 2021
Currently, there are no mass-produced cars that have achieved L3 to L5 autonomy. The most advanced readily available technologies are Super Cruise by GM and Autopilot by Tesla, which fall into the L2+ category.
Global forecasts estimate tremendous growth in sales of autonomous vehicles (L4 and L5) between 2025 and 2035—from just under 1 million units in 2026 to 21 million units in 2035.
The Autonomous Vehicle Software Stack
At a basic level, the autonomous vehicle software stack is powered by sensors (including LiDAR, cameras, etc.) that feed data to AV software algorithms, which make split-second driving decisions. Firmware plays a crucial role in the tech stack in many different ways. For example, it is responsible for securely booting the real-time operating system and ensuring that various hardware components are operational. In addition, firmware can also be responsible for providing overall system diagnostic data, which is crucial in determining the overall health and safety of the AV system.
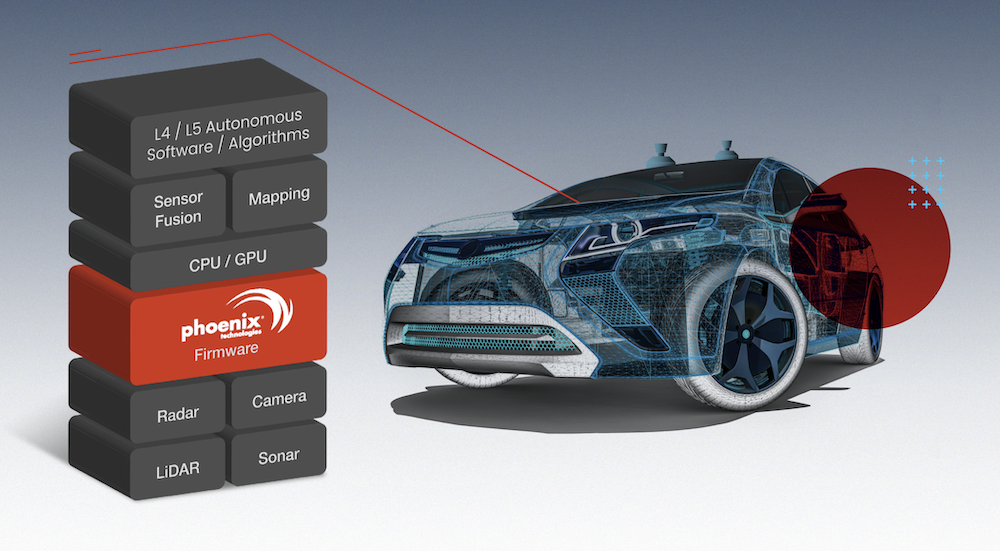
The Three Areas of AV Compute
The autonomous vehicle software stack includes at least three areas of compute, each of which supports different vehicle systems. ECUs (Electronic Control Units) and their associated microcontrollers were the first compute systems in vehicles introduced in the late ‘70s and ‘80s. Modern infotainment systems, characterized by large in-car displays, became ubiquitous in the 2010s. The most recent innovation is autonomous compute, which will undoubtedly continue to emerge in the 2020s and beyond. The line between these areas of compute is sure to blur over time, but they will all continue to contribute to the evolution of modern vehicles.
| Microcontrollers (ECUs) | Infotainment | Autonomous | |
| Definition | Electronic Control Units (ECUs) feature embedded microcontrollers that handle one or more individual vehicle functions. | The display and underlying vehicle systems that combine entertainment and information delivery to drivers and passengers. | Sophisticated, compute-intensive software and algorithms that process high-speed feeds from sensors to make split-second driving decisions. |
| Examples |
|
|
|
Microcontrollers (ECUs)
Electronic Control Units (ECUs) feature embedded microcontrollers that handle one or more individual vehicle functions.
- Automatic transmission
- Braking
- Power doors
Infotainment
The display and underlying vehicle systems that combine entertainment and information delivery to drivers and passengers.
- Entertainment
- GPS
- Climate
Autonomous
Sophisticated, compute-intensive software and algorithms that process high-speed feeds from sensors to make split-second driving decisions.
- L1-L2 advanced driver assistance system (ADAS)
- L3-L5 autonomous software/ algorithms
Autonomous Vehicle Software Stack Expertise
Every computing device has firmware, and the technology that powers AV is no exception to this rule. Firmware provides the low-level control that runs the hardware on a device. The firmware configures and initializes the hardware to run the operating system and then provides the interface to run normal operations on the hardware.
The sad truth is that many manufacturers view firmware as a commodity part that isn’t worthy of high-level executive attention. Firmware is not the eye-catching new technology making AV so appealing—it’s the fundamental component making everything else work. But it’s precisely this obscurity that has made firmware such an attractive target. Since firmware is the first piece within the autonomous vehicle software stack that executes when a vehicle’s AV system boots, attackers targeting firmware can quickly escalate a serious attack across numerous AV systems and cause catastrophic harm.
In this blog series, although we focus on the development and security of firmware that powers L4/L5 autonomous compute systems, these principles can (and should) be applied to every level of autonomy.