Over the last century, vehicles have become increasingly connected and computerized, with the future promising complete L4/L5 autonomy. The complex software required to run these vehicles all sits on top of firmware, which has been facing an exponential increase in cyberthreats over the last few years. In addition to increased firmware threats, increased connectivity across all autonomous vehicle (AV) systems create a significantly expanded attack surface area. Firmware infiltration can give hackers the highest level of access to an autonomous driving system’s critical components, allowing them to inflict severe damage—from overriding safety protocols to taking complete control.
 It’s important to remember how rapidly technology has infiltrated modern vehicles. Whether luxury upgrade or essential safety feature, new technology often relies on yet another connected system, providing another avenue through which malicious actors can attack.
It’s important to remember how rapidly technology has infiltrated modern vehicles. Whether luxury upgrade or essential safety feature, new technology often relies on yet another connected system, providing another avenue through which malicious actors can attack.
Autonomous vehicle engineers must take a proactive approach to firmware security from the beginning of the development process and perform ongoing risk mitigation to protect their products.
The Autonomous Vehicle Cybersecurity Landscape
Firmware has become a primary point of attack across all industries. As modern vehicles evolve to become more connected and fully autonomous, the potential impacts of a security breach cannot be ignored.Increasing Firmware Vulnerabilities
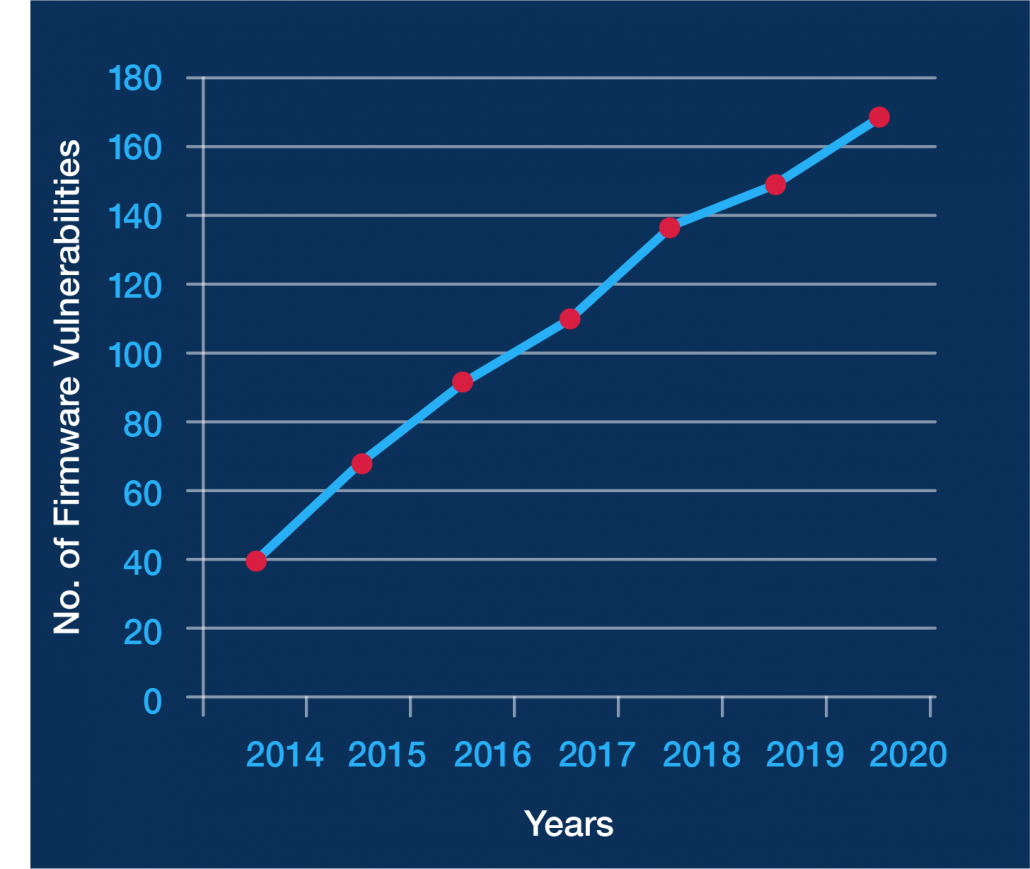
Every computing device has firmware, and autonomous vehicles are no exception to this rule. As the number of firmware vulnerabilities continues to increase, the risk for AV-related breaches increases in tandem. This graph shows the total (through 2020) number of known medium-, critical- and high-risk firmware vulnerabilities tracked by Phoenix, based on the Common Vulnerability Scoring System (CVSS). As the graph shows, the number of vulnerabilities has been climbing steadily, more than quadrupling in less than six years. It’s important to remember how rapidly technology has infiltrated modern vehicles. Whether luxury upgrade or essential safety feature, new technology often relies on yet another connected system, providing another avenue through which malicious actors can attack.
It’s important to remember how rapidly technology has infiltrated modern vehicles. Whether luxury upgrade or essential safety feature, new technology often relies on yet another connected system, providing another avenue through which malicious actors can attack.
For example, today’s cars have up to 150 electronic control units (ECUs) and about 100 million lines of code. By 2023, that number is expected to increase to 300 million lines of code.
Attack Vectors and Security Gaps
The large attack surface area inherent in autonomous vehicles makes them particularly vulnerable. For example, the required connectivity needed to run advanced autonomous vehicle systems means that vehicles could be hacked through:- Vehicle to anything (V2X) technology
- Personal area networks (PANs)
- Controller area networks (CANs)
- Open OBD ports
- Tampering with ECUs
- Rouge updates
- Management mode manipulation
- Supply chain attacks
It’s Time to Take a Proactive Approach to Autonomous Vehicle Cybersecurity
Autonomous vehicle OEMs must take a proactive approach to firmware security. This includes ensuring complete security across every firmware component, from development to ongoing risk mitigation and patching. They need to develop and implement internal processes to protect themselves and ensure safety for drivers. Selling vehicles that are later revealed to have vulnerabilities is expensive and scars the company’s reputation.
Firmware Design and Development
Firmware development is a resource-intense project. Considering the numerous interacting systems and devices within a single autonomous vehicle can get very complicated very fast. However, implementing robust autonomous vehicle cybersecurity at the firmware level is the first defense against any type of attack. Given the recent developments in autonomous vehicles, especially at the L4 and L5 levels, it is particularly challenging to find individuals or teams with the right expertise.Ongoing Risk Mitigation
Many organizations don’t have the resources or expertise required to develop highly advanced and secure firmware. Luckily, there are numerous public sector organizations and industry groups that have already done a lot of work to mitigate firmware risk:- Unified Extensible Firmware Interface (UEFI) Forum
- Trusted Computing Group (TCG)
- Automotive Cybersecurity Industry Consortium (ACIC)
- Automotive Information Sharing and Analysis Center (Auto-ISAC)
- Alliance for Automotive Innovation
- SAE International
These organizations work to develop and promote firmware standards and specifications to cover security on an ongoing basis.However, even with various industry bodies establishing automotive security protocols and specifications, OEMs are still responsible for:
- Designing secure firmware based on existing best practices
- Implementing recommendations and standards
- Monitoring for specifications and vulnerabilities
- Building and distributing patches for vulnerabilities as they emerge
Your autonomous vehicles could be left vulnerable to attack without the proper in-house expertise. Partner with Phoenix Technologies for outsourced autonomous vehicle cybersecurity expertise from initial secure firmware design and development to ongoing risk mitigation and monitoring.
Outsource Autonomous Vehicle Cybersecurity
Phoenix Technologies offers a solution with comprehensive AV firmware development services and ongoing risk mitigation tools. By leveraging Phoenix’s expertise, OEMs can take a proactive approach to firmware security from the very beginning and have the tools needed to remediate vulnerabilities to better protect themselves and end users.Design and Development Services
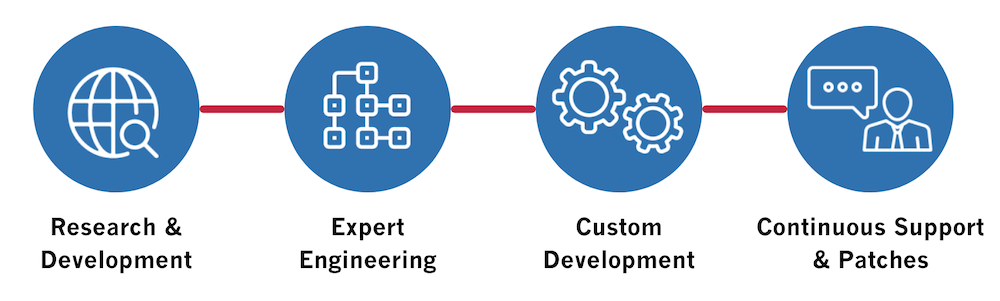
At Phoenix, we partner with you throughout the entire firmware life cycle, from the initial development and deployment through post-production support and ongoing security.- Research & Development
- Customer Engagement
- Production & Delivery
- Post-Production Support
Robust Risk Mitigation
Phoenix offers a security subscription service that helps manufacturers track and remediate firmware vulnerabilities. The Phoenix FirmCare security-as-a-service program is an annual support package that includes the monitoring and notification of identified firmware vulnerabilities. Partners who leverage Phoenix firmware can also take advantage of rapid patch creation and delivery to ensure that firmware and the vehicles running on it stay protected. The program includes:- Constant monitoring
- Regularly scheduled reports
- White hat hacking
- Penetration testing